Post by AskApache | Mar 06, 2024
 .htaccess is a very ancient configuration file for web servers, and is one of the most powerful configuration files most webmasters will ever come across. This htaccess guide shows off the very best of the best htaccess tricks and code snippets from hackers and server administrators.
.htaccess is a very ancient configuration file for web servers, and is one of the most powerful configuration files most webmasters will ever come across. This htaccess guide shows off the very best of the best htaccess tricks and code snippets from hackers and server administrators.
You've come to the right place if you are looking to acquire mad skills for using .htaccess files!
Apache Hosting Htaccess Optimization Security SEO Web Development WordPress .htpasswd 301 Redirect Apache Apache HTTP Server Cache Hosting Htaccess
Apr 14, 2022
 What if you'd like to send a 200 OK response instead of the default 404 Not Found response using Apache
What if you'd like to send a 200 OK response instead of the default 404 Not Found response using Apache .htaccess files or httpd.conf? One use would be to make sure upstream caches cache any request on an api server, as 404's are not cached.
Apache Htaccess 404 ErrorDocument Redirect
Mar 03, 2022
 htaccess rewrite Master Class! If you understand the basics of mod_rewrite, or if you literally write the mod_rewite.c code, this article will transform your thinking. The transformation is profound. Deeply effective. Culmination of the best of the best mod_rewrite tricks for understanding and learning exactly what rewrite is doing.
htaccess rewrite Master Class! If you understand the basics of mod_rewrite, or if you literally write the mod_rewite.c code, this article will transform your thinking. The transformation is profound. Deeply effective. Culmination of the best of the best mod_rewrite tricks for understanding and learning exactly what rewrite is doing.
Htaccess Htaccess mod_rewrite PHP RewriteCond RewriteRule
Apr 04, 2020
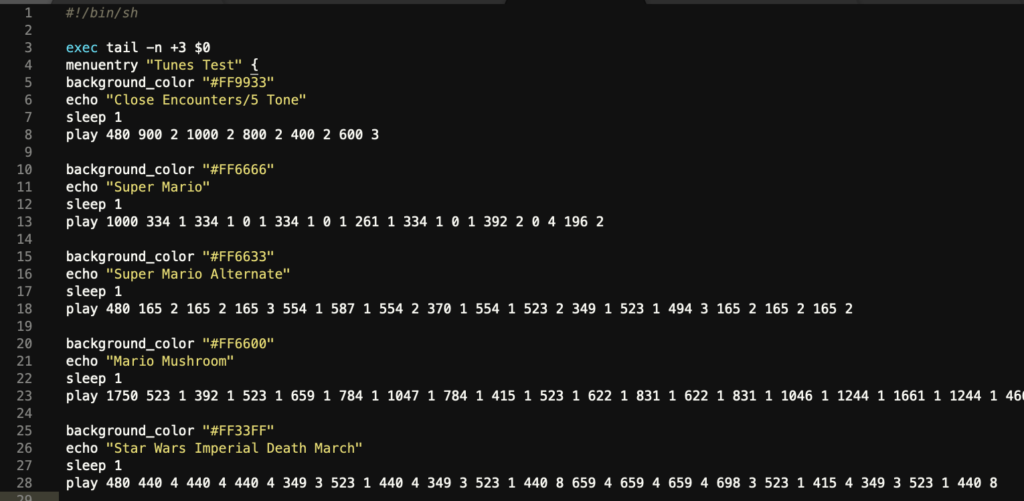 Play a tune directly on your pcspeaker right before the grub boot manager loads.
Play a tune directly on your pcspeaker right before the grub boot manager loads.
Linux GRUB GRUB_INIT_TUNE grub.cfg speaker
Jan 24, 2020
I really really wanted to run the latest MariaDB with LZ4 Page Compression.. it is a game changer for many types of large databases I deal with. So I compiled it manually in a way that is repeatable and follows best-practices and it's now powering this site. Now I can use InnoDB Page Compression with lzo, lzma, bzip2, snappy, or my favorite algorithm: LZ4.

Thought this would be a good chance to post a howto, and show that there is a lot you can do by compiling software yourself and breaking the package management one-click install shackles.
Linux MySQL centos compression InnoDB lz4 MariaDB MySQL
Oct 30, 2019
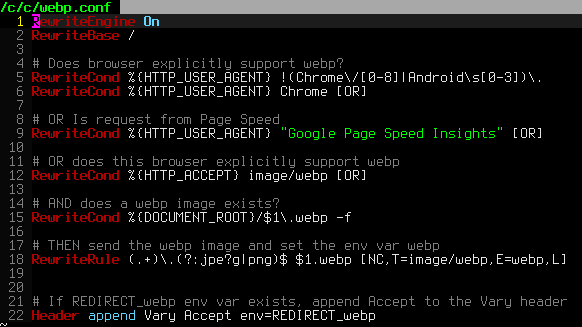
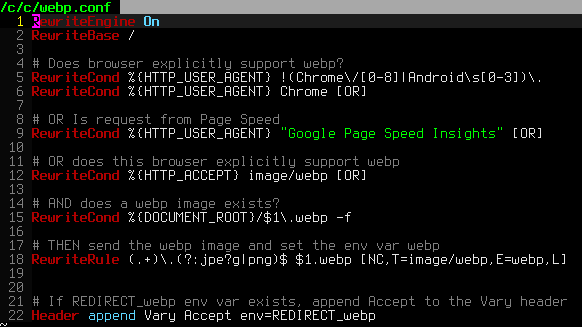 One of the biggest speed bottlenecks of sites today are images, specifically unoptimized images or large scaled images. With Apaches Rewrite module we can convert all existing jpegs and png files (and most gifs) to webp, then transparently rewrite them so that a request for img.png from a browser that supports webp will receive img.webp.
One of the biggest speed bottlenecks of sites today are images, specifically unoptimized images or large scaled images. With Apaches Rewrite module we can convert all existing jpegs and png files (and most gifs) to webp, then transparently rewrite them so that a request for img.png from a browser that supports webp will receive img.webp.
Hosting Htaccess Optimization accept Header png RewriteCond RewriteRule vary webp
Mar 03, 2018
The bottom line for this article is that I want to make WordPress as fast, secure, and easy to install, run, and manage because I am using it more and more for client production sites, I will work for days in order to solve an issue so that I never have to spend time on that issue again. Time is money in this industry and that is ultimately (time) what there is to gain by tweaking WordPress.
Note: I spent no time on readability, this is primarily a read the code and figure it out article.. This is for advanced users looking for a reference or discussion and for those of you looking to advance. Feedback would be great if you make it that far..
WordPress wordpress wp-config.php
Jan 06, 2018
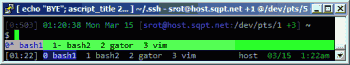 This amazing bash linux prompt does more than meets the eye. If you want to know how to become really good with technology, linux is the secret sauce behind the AskApache articles. Open Source is elixir of the web. Thanks to everyone who helped me for the past 20 years. I use linux/bsd because homey don't play, so this is geared to be as productive a prompt as I can make it.
This amazing bash linux prompt does more than meets the eye. If you want to know how to become really good with technology, linux is the secret sauce behind the AskApache articles. Open Source is elixir of the web. Thanks to everyone who helped me for the past 20 years. I use linux/bsd because homey don't play, so this is geared to be as productive a prompt as I can make it.
Don't have much time.. or just don't care? Not a problem, here are the 3 lines to copy and paste - you can just paste them right in your shell to test it, or add to a startup script.
export AA_P="export PVE=\"\\033[m\\033[38;5;2m\"\$(( \`sed -n \"s/MemFree:[\\t ]\\+\\([0-9]\\+\\) kB/\\1/p\" /proc/meminfo\` / 1024 ))\"\\033[38;5;22m/\"\$((\`sed -n \"s/MemTotal:[\\t ]\\+\\([0-9]\\+\\) kB/\\1/p\" /proc/meminfo\`/ 1024 ))MB\"\\t\\033[m\\033[38;5;55m\$(< /proc/loadavg)\\033[m\";echo -en \"\""
export PROMPT_COMMAND="history -a;((\$SECONDS % 10==0 ))&&eval \"\$AA_P\";echo -en \"\$PVE\";"
export PS1="\\[\\e[m\\n\\e[1;30m\\][\$\$:\$PPID \\j:\\!\\[\\e[1;30m\\]]\\[\\e[0;36m\\] \\T \\d \\[\\e[1;30m\\][\\[\\e[1;34m\\]\\u@\\H\\[\\e[1;30m\\]:\\[\\e[0;37m\\]\${SSH_TTY} \\[\\e[0;32m\\]+\${SHLVL}\\[\\e[1;30m\\]] \\[\\e[1;37m\\]\\w\\[\\e[0;37m\\] \\n(\$SHLVL:\\!)\\\$ " && eval $AA_PLinux bash Prompt PROMPT_COMMAND PS1 sed ssh
Jan 04, 2018
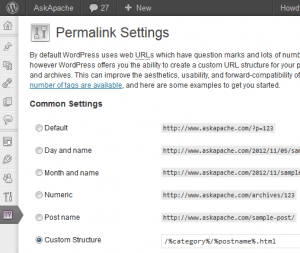 WordPress uses a file named
WordPress uses a file named .htaccess to rewrite all requests to the main index.php file. This article explains what the htaccess file rules look like and what they actually do.
Htaccess Htaccess wordpress
 .htaccess is a very ancient configuration file for web servers, and is one of the most powerful configuration files most webmasters will ever come across. This htaccess guide shows off the very best of the best htaccess tricks and code snippets from hackers and server administrators.
.htaccess is a very ancient configuration file for web servers, and is one of the most powerful configuration files most webmasters will ever come across. This htaccess guide shows off the very best of the best htaccess tricks and code snippets from hackers and server administrators.






