Libcurl Error Codes


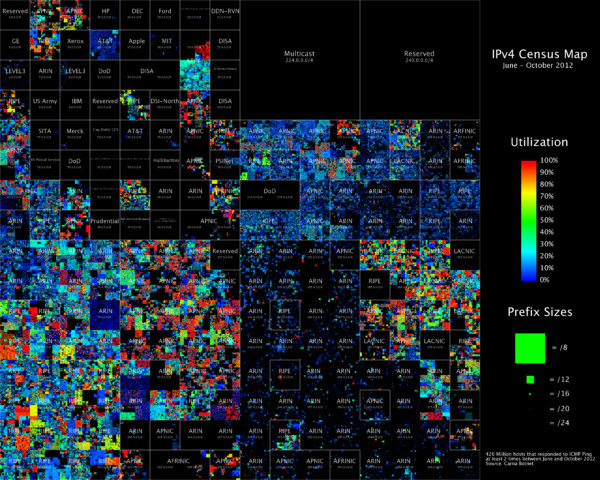 While playing around with the Nmap Scripting Engine (NSE) we discovered an amazing number of open embedded devices on the Internet. Many of them are based on Linux and allow login to standard BusyBox with empty or default credentials. We used these devices to build a distributed port scanner to scan all IPv4 addresses. These scans include service probes for the most common ports, ICMP ping, reverse DNS and SYN scans. We analyzed some of the data to get an estimation of the IP address usage.
While playing around with the Nmap Scripting Engine (NSE) we discovered an amazing number of open embedded devices on the Internet. Many of them are based on Linux and allow login to standard BusyBox with empty or default credentials. We used these devices to build a distributed port scanner to scan all IPv4 addresses. These scans include service probes for the most common ports, ICMP ping, reverse DNS and SYN scans. We analyzed some of the data to get an estimation of the IP address usage.
 This trailer speaks to the current state of the Internet of Things, and what we can expect over the next several years.
This trailer speaks to the current state of the Internet of Things, and what we can expect over the next several years.
 Stop wasting your lives with Mac Terminals.. or Macs. Get a real machine and then get a real shell multiplexer! For many years we all loved GNU Screen, but tmux is by far a better option today. The only time I am in the shell and not using a multiplexer, is when I'm not on one of my machines. My Arch Linux machines all run URxvt and my .bash_profiles all start tmux automataically, whether in X or single-user mode, tmux is where it's at.
Stop wasting your lives with Mac Terminals.. or Macs. Get a real machine and then get a real shell multiplexer! For many years we all loved GNU Screen, but tmux is by far a better option today. The only time I am in the shell and not using a multiplexer, is when I'm not on one of my machines. My Arch Linux machines all run URxvt and my .bash_profiles all start tmux automataically, whether in X or single-user mode, tmux is where it's at.
 Well, not this sites server, which has never been hacked, but a server hosted with hostgator.
Well, not this sites server, which has never been hacked, but a server hosted with hostgator.
Interestingly, the hacker sent me an email and left me an mp3, which I've uploaded for your listening leisure.
Do real hackers exist? Yes. Can we coexist? Preferably!
Secure WP Super Cache, Anti-exploits, Mitigation techniques. A bunch of current ways to stop wordpress exploits and spam. 
Love this Tchaikovsky Violin Concerto in D Major by Jinjoo Cho. It's a beautiful take on the classic.
The following is just a quick but detailed reference of some of the commands I used to successfully uninstall cpanel permanently. This is for advanced users of the shell. If you run a single one of these commands without fully understanding it, you will probably kill your server, lose everything on it permanently, not have a website or email for weeks.. So backup everything. FIRST. You should also contact your hosting provider support - but be prepared for some MAJOR negativity.. cpanel makes things very easy for web-hosting companies, and you are less than a drop in their bucket.
....
This is our world now... the world of the electron and the switch, the
beauty of the baud. We make use of a service already existing without paying
for what could be dirt-cheap if it wasn't run by profiteering gluttons, and
you call us criminals. We explore... and you call us criminals. We seek
after knowledge... and you call us criminals. We exist without skin color,
without nationality, without religious bias... and you call us criminals.
You build atomic bombs, you wage wars, you murder, cheat, and lie to us
and try to make us believe it's for our own good, yet we're the criminals.
....
The proponents of this scheme have given it names such as "trusted computing" and "palladium". We call it "treacherous computing", because the effect is to make your computer obey companies instead of you. This was implemented in 2007 as part of Windows Vista; we expect Apple to do something similar. In this scheme, it is the manufacturer that keeps the secret code, but the FBI would have little trouble getting it.
SOPA: Anonymous Lists Their Demands
A rallying cry on the occassion of the Web's first mass blackout
As we watch the web go dark today in protest against the SOPA/PIPA censorship bills, let's take a moment and reflect on why this fight is so important. We may have learned that free speech is what makes America great, or instinctively resist attempts at silencing our voices. But these are abstract principles, divorced from the real world and our daily lives.
Free speech is the foundation of a free society. We can have the vote all we want. We can donate money wherever we want. But unless we're able to talk to each other and figure out collectively _what_ we want, those things don't matter.
We believe a healthy society doesn't allow its artists, musicians and other creators to starve. The copyright industry has been justly criticized for abusing the political process in a desperate attempt to maintain its role as a cultural gatekeeper, a business model made obsolete by a digital age of free copies. But the RIAA, MPAA & IFPI deserve our opprobrium for making enormous profits while often leaving the very artists it claims to represent *poorer* than they would be as independents.[1] While the public may have greater access to the few artists deemed sufficiently marketable to gain mass media promotion, fewer and fewer of us are making art and music in our own lives.
We call upon all freedom loving Internauts to join us. We further call upon our legislators, bureaucrats and the media & telecommunications industries to immediately begin implementing our demands. The future of free speech is bright, and clear - either stand with us or get out of the way.
PirateBay Press Release regarding SOPA...
So, the whole basis of this industry, that today is screaming about losing control over immaterial rights, is that they circumvented immaterial rights. They copied (or put in their terminology: "stole") other peoples creative works, without paying for it. They did it in order to make a huge profit. Today, they're all successful and most of the studios are on the Fortune 500 list of the richest companies in the world. Congratulations - it's all based on being able to re-use other peoples creative works. And today they hold the rights to what other people create. If you want to get something released, you have to abide to their rules. The ones they created after circumventing other peoples rules.
The reason they are always complainting about "pirates" today is simple. We've done what they did. We circumvented the rules they created and created our own. We crushed their monopoly by giving people something more efficient. We allow people to have direct communication between eachother, circumventing the profitable middle man, that in some cases take over 107% of the profits (yes, you pay to work for them). It's all based on the fact that we're competition. We've proven that their existance in their current form is no longer needed. We're just better than they are.
Oh ya lets get it on! short but sweet
Ok I just came back up to write the intro.. I'm trying to keep it short to avoid getting bogged down by the coolness of each step. Here is what goes on. When I logon to my XP machine at work, I bring my usb key and plug it in first. On logging a window pops up first and it's a password prompt to mount my encrypted drive leonardo. It also checks a keyfile that is located on my usb key, but all I do now is type in my password. That causes my encrypted folder to be accessible to me like a normal drive, and it autoruns a startup batch file.
The batch file causes Portable versions of Firefox (all my bookmarks, my settings) to load, and launches Portable Mozilla Thunderbird (IMAP makes this work well), which is my favorite program (great GPG features and open-source!). Also Some Adobe CS4 software is loaded from the hard drive, like DreamWeaver. In the background, a service we created executes a PortaPuttY plink command to create forwarded tunnels from various remote servers and accounts, all using key-based encryption. These tunnels are automatically reconnected if they are disconnected, meaning you can use a socks 5 if you want or even better!
Ever wanted to execute commands on your server through php? Now you can. I'm calling this file (see below) shell.php and it allows you to run commands on your web server with the same permissions that your php executable has.
I've had a lot of people ask about the FeedBurner FeedCount image on AskApache. Specifically how to set it up with custom messages and different colors each page view... It is pretty sweet..
thought I'd take a break from coding and post about how open-source is such a great tool for finding the best answers to the toughest questions,
/** is the status code informational */ #define ap_is_HTTP_INFO(x) (((x) >= 100)&&((x) < 200)) /** is the status code OK ?*/ #define ap_is_HTTP_SUCCESS(x) (((x) >= 200)&&((x) < 300)) /** is the status code a redirect */ #define ap_is_HTTP_REDIRECT(x) (((x) >= 300)&&((x) < 400)) /** is the status code a error (client or server) */ #define ap_is_HTTP_ERROR(x) (((x) >= 400)&&((x) < 600)) /** is the status code a client error */ #define ap_is_HTTP_CLIENT_ERROR(x) (((x) >= 400)&&((x) < 500)) /** is the status code a server error */ #define ap_is_HTTP_SERVER_ERROR(x) (((x) >= 500)&&((x) < 600)) /** is the status code a (potentially) valid response code? */ #define ap_is_HTTP_VALID_RESPONSE(x) (((x) >= 100)&&((x) < 600))
 I have been in some tight spots where I had to sniff a password or two off the wire, or sniff some packets off the wire and based on the packets content perform some action... Accidentally, I stumbled on a method to sniff data while remaining undetected and invisible.
I have been in some tight spots where I had to sniff a password or two off the wire, or sniff some packets off the wire and based on the packets content perform some action... Accidentally, I stumbled on a method to sniff data while remaining undetected and invisible.
 There isn't much vlan info on the net in terms of specifics and I had to learn all about it because I needed to log in to a switch that was on a different vlan. With the help of the Ettercap developers NaGA and ALoR I figured it out.
There isn't much vlan info on the net in terms of specifics and I had to learn all about it because I needed to log in to a switch that was on a different vlan. With the help of the Ettercap developers NaGA and ALoR I figured it out.
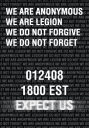 For the good of your followers,
For the good of your followers,
for the good of mankind,
and for our own enjoyment,
we shall proceed to expel you from the Internet and systematically dismantle the Church of Scientology in its present form.
Yes, it's true! I'm the author of ping for UNIX. Ping is a little thousand-line hack that I wrote in an evening which practically everyone seems to know about. :-)
This quick tutorial will show you the steps to change and reset any user password on a windows computer, and also show you how to protect your computer from people doing this to you!
Caching with .htaccess and Apache will take your website and your web skills to the next level. This is some technical and advanced methods condensed to simple htaccess code examples for you.
 AskApache caters to the web/system elite, who's skillsets are also good for online stock trading. Heres a look at a penny stock investment.
AskApache caters to the web/system elite, who's skillsets are also good for online stock trading. Heres a look at a penny stock investment.