.htaccess Plugin Blocks Spam, Hackers, and Password Protects Blog
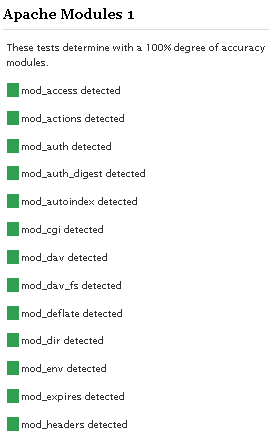
Well what can I say, other than this is sooo DOPE! Here is a list of the modules this plugin (version 4.7 unreleased) will automatically detect. I compiled the list myself using every module included with any default Apache installation for ALL the versions listed below, 1.3 to 2.2+
Want to know something else I'm including in this plugin? For each and every module that is detected, this plugin can then detect ALL of the modules .htaccess Directives! For instance, RewriteRule, AccessFileName, AddHandler, etc.. are each a directive belonging to a module that is allowed to be used from within .htaccess files.
Talk about sick.. these tricks have the diamond disease!
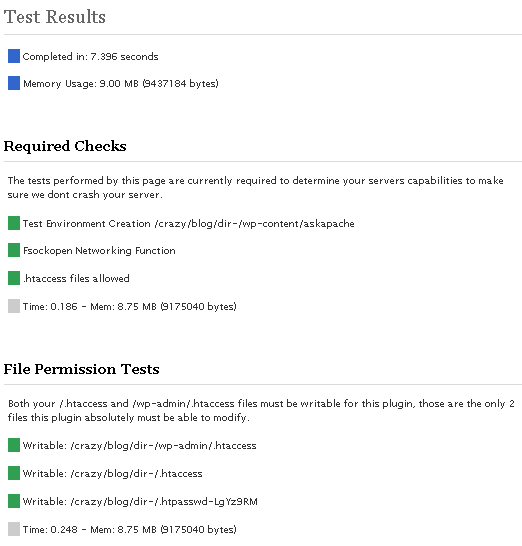
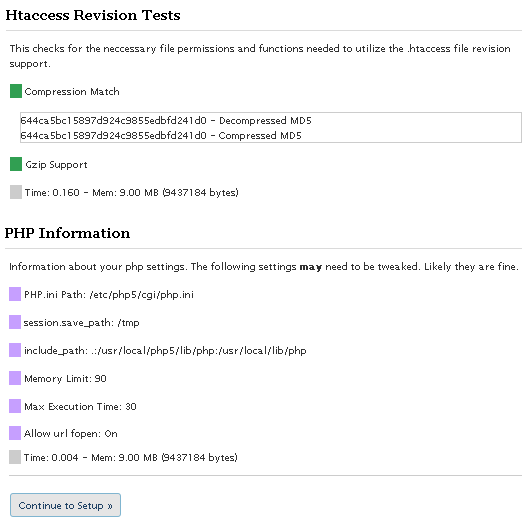
Screenshot Unreleased 4.7
I've been making a lot of progress as these screenshots illustrate, including the ability to detect 100% accurately the modules that are enabled on your server. Big deal! you might say... "How does knowing the modules help?"
Well it just so happens that in addition to detecting which modules are loaded on your server, this plugin will also detect which Directives are enabled for each module that are allowed to be used from within your .htaccess file! Future release will provide the ability to explore the different .htaccess directives allowed by your server, so you can do all sorts of cool Apache .htaccess tricks to secure your blog and make it run better.
Apache Module Detection
Future releases of this plugin will also let you search for non-default modules, wild, beta, and others.
- mod_access
- mod_actions
- mod_alias
- mod_asis
- mod_auth
- mod_auth_anon
- mod_auth_basic
- mod_auth_dbm
- mod_auth_digest
- mod_auth_ldap
- mod_authn_alias
- mod_authn_anon
- mod_authn_dbd
- mod_authn_dbm
- mod_authn_default
- mod_authn_file
- mod_authnz_ldap
- mod_authz_dbm
- mod_authz_default
- mod_authz_groupfile
- mod_authz_host
- mod_authz_owner
- mod_authz_user
- mod_autoindex
- mod_bucketeer
- mod_cache
- mod_case_filter
- mod_case_filter_in
- mod_cern_meta
- mod_cgi
- mod_cgid
- mod_charset_lite
- mod_dav
- mod_dav_fs
- mod_dav_lock
- mod_dbd
- mod_deflate
- mod_dir
- mod_disk_cache
- mod_dumpio
- mod_echo
- mod_env
- mod_example
- mod_expires
- mod_ext_filter
- mod_file_cache
- mod_filter
- mod_headers
- mod_ident
- mod_imagemap
- mod_imap
- mod_include
- mod_info
- mod_isapi
- mod_log_config
- mod_log_forensic
- mod_logio
- mod_mem_cache
- mod_mime
- mod_mime_magic
- mod_mycore
- mod_negotiation
- mod_netware
- mod_nw_ssl
- mod_optional_fn_export
- mod_optional_fn_import
- mod_optional_hook_export
- mod_optional_hook_import
- mod_proxy
- mod_proxy_ajp
- mod_proxy_balancer
- mod_proxy_connect
- mod_proxy_ftp
- mod_proxy_http
- mod_rewrite
- mod_security
- mod_setenvif
- mod_so
- mod_speling
- mod_ssl
- mod_status
- mod_substitute
- mod_suexec
- mod_test
- mod_unique_id
- mod_userdir
- mod_usertrack
- mod_version
- mod_vhost_alias
- mod_win32
The original plugin page and description can be found here.
UPDATE: 11/22/08
To make a long story short, I downloaded each major release of the apache httpd source code from version 1.3.0 to version 2.2.10, then I configured and compiled each for a custom HTTPD installation built from source. This allowed me to find every directive allowed in .htaccess files for each particular version. YES!
http://wordpress.org/support/rss/topic/214390
I've been working on a completely improved version on/off for about a month with the specific goal of finally ending all the little errors that can crop up when dealing with .htaccess. To that effect I am succeeding marvelously, first I've converted the plugin to a class (4+5 compat), I've replaced my error_handling with WordPress's WP_Error class, and the coolest change is the new tests I've added. To make a long story short, I downloaded each major release of the apache httpd source code starting at version 1.3.0 and finishing with version 2.2.10, I then compiled each version and built a HTTPD from source for all the apache versions.1.3.0,1.3.1,1.3.11,1.3.12,1.3.14,1.3.17,1.3.19,1.3.2,1.3.20,1.3.22,1.3.23,1.3.24,1.3.27,1.3.28,1.3.29,1.3.3,1.3.31,1.3.32,1.3.33,1.3.34,1.3.35,1.3.36,1.3.37,1.3.39,1.3.4,1.3.41,1.3.6,1.3.9,2.0.35,2.0.36,2.0.39,2.0.40,2.0.42,2.0.43,2.0.44,2.0.45,2.0.46,2.0.47,2.0.48,2.0.49,2.0.50,2.0.51,2.0.52,2.0.53,2.0.54,2.0.55,2.0.58,2.0.59,2.0.61,2.0.63,2.1.3-beta,2.1.6-alpha,2.1.7-beta,2.1.8-beta,2.1.9-beta,2.2.0,2.2.10,2.2.2,2.2.3,2.2.4,2.2.6,2.2.8,2.2.9Then I went through each version and determined the compatible modules for that version, and I'm pretty confident that I was also able to find each and every directive allowed by the compatible modules for that version (including core directives). See .htaccess directive list. Basically I can now test a server using a variety of methods and determine almost 100% accurately what version of Apache (down to the API) is running, what modules (and versions) are enabled, and each and every directive that is allowed or disallowed for that version. So this is so awesome because now we can enable all sorts of additional security features. Other big changes are:And this time I am developing the plugin using a plethora of wordpress installations and configurations, to make sure that it will work regardless of a custom siteurl, blogid, etc.. Release will come before 2009.. I have some vacations to take and business to finish first.
- Completely hands-off updates, so that updating the plugin keeps all your settings.
- making each SID module have its own configuration and options (like protecting individual files, individual request, and custom exploit strings).
- Advanced ErrorDocument usage and handling (like tracking repeat offenders and suggesting they be blocked, emailing admin with custom info, etc..)
- Multi User/Group password Control
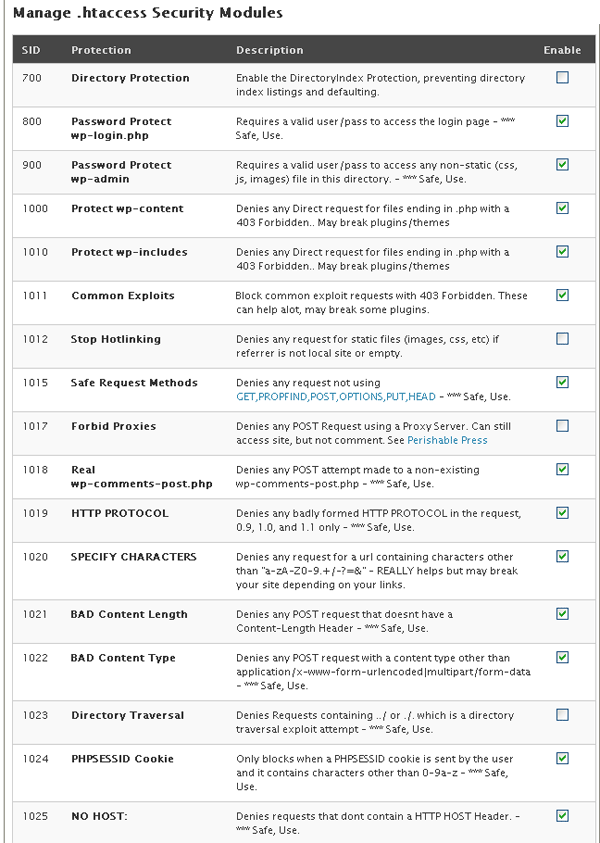
.htaccess Security Modules
Directory Protection
Enable the DirectoryIndex Protection, preventing directory index listings and defaulting. [Disable]
Options -Indexes DirectoryIndex index.html index.php /index.php
Password Protect wp-login.php
Requires a valid user/pass to access the login page - *** Safe, Use [401]
Order Deny,Allow Deny from All Satisfy Any AuthName "Protected By AskApache" AuthUserFile /web/askapache.com/.htpasswda1 AuthType Basic Require valid-user
Password Protect wp-admin
Requires a valid user/pass to access any non-static (css, js, images) file in this directory. - *** Safe, Use [401]
Options -ExecCGI -Indexes +FollowSymLinks -Includes DirectoryIndex index.php /index.php Order Deny,Allow Deny from All Satisfy Any AuthName "Protected By AskApache" AuthUserFile /web/askapache.com/.htpasswda1 AuthType Basic Require valid-userAllow from All SecFilterEngine Off Allow from All
Protect wp-content
Denies any Direct request for files ending in .php with a 403 Forbidden.. May break plugins/themes [401]
RewriteCond %{THE_REQUEST} ^[A-Z]{3,9}\ /wp-content/.*$ [NC]
RewriteCond %{REQUEST_FILENAME} !^.+flexible-upload-wp25js\.php$
RewriteCond %{REQUEST_FILENAME} ^.+\.(php|html|htm|txt)$
RewriteRule .* - [F,NS,L]
Protect wp-includes
Denies any Direct request for files ending in .php with a 403 Forbidden.. May break plugins/themes [403]
RewriteCond %{THE_REQUEST} ^[A-Z]{3,9}\ /wp-includes/.*$ [NC]
RewriteCond %{THE_REQUEST} !^[A-Z]{3,9}\ /wp-includes/js/.+/.+ HTTP/ [NC]
RewriteCond %{REQUEST_FILENAME} ^.+\.php$
RewriteRule .* - [F,NS,L]
Common Exploits
Block common exploit requests with 403 Forbidden. These can help alot, may break some plugins. [403]
RewriteCond %{REQUEST_URI} !^/(wp-login\.php|wp-admin/|wp-content/plugins/|wp-includes/).* [NC]
RewriteCond %{THE_REQUEST} ^[A-Z]{3,9}\ ///.* HTTP/ [NC,OR]
RewriteCond %{THE_REQUEST} ^[A-Z]{3,9}\ /.*?=?(http|ftp|ssl|https):/.* HTTP/ [NC,OR]
RewriteCond %{THE_REQUEST} ^[A-Z]{3,9}\ /.*??.* HTTP/ [NC,OR]
RewriteCond %{THE_REQUEST} ^[A-Z]{3,9}\ /.*\.(asp|ini|dll).* HTTP/ [NC,OR]
RewriteCond %{THE_REQUEST} ^[A-Z]{3,9}\ /.*\.(htpasswd|htaccess|aahtpasswd).* HTTP/ [NC]
RewriteRule .* - [F,NS,L]
Stop Hotlinking
Denies any request for static files (images, css, etc) if referrer is not local site or empty. [403]
RewriteCond %{HTTP_REFERER} !^$
RewriteCond %{REQUEST_URI} !^/(wp-login\.php|wp-admin/|wp-content/plugins/|wp-includes/).* [NC]
RewriteCond %{HTTP_REFERER} !^http://www\.askapache\.com.*$ [NC]
RewriteRule \.(ico|pdf|flv|jpg|jpeg|mp3|mpg|mp4|mov|wav|wmv|png|gif|swf|css|js)$ - [F,NS,L]
Safe Request Methods
Denies any request not using GET,PROPFIND,POST,OPTIONS,PUT,HEAD - *** Safe, Use [403]
RewriteCond %{REQUEST_METHOD} !^(GET|HEAD|POST|PROPFIND|OPTIONS|PUT)$ [NC]
RewriteRule .* - [F,NS,L]
Forbid Proxies
Denies any POST Request using a Proxy Server. Can still access site, but not comment. See Perishable Press [403]
RewriteCond %{REQUEST_METHOD} =POST
RewriteCond %{HTTP:VIA}%{HTTP:FORWARDED}%{HTTP:USERAGENT_VIA}%{HTTP:X_FORWARDED_FOR}%{HTTP:PROXY_CONNECTION} !^$ [OR]
RewriteCond %{HTTP:XPROXY_CONNECTION}%{HTTP:HTTP_PC_REMOTE_ADDR}%{HTTP:HTTP_CLIENT_IP} !^$
RewriteCond %{REQUEST_URI} !^/(wp-login\.php|wp-admin/|wp-content/plugins/|wp-includes/).* [NC]
RewriteRule .* - [F,NS,L]
Real wp-comments-post.php
Denies any POST attempt made to a non-existing wp-comments-post.php - *** Safe, Use [403]
RewriteCond %{THE_REQUEST} ^[A-Z]{3,9}\ /.*/wp-comments-post\.php.* HTTP/ [NC]
RewriteRule .* - [F,NS,L]
HTTP PROTOCOL
Denies any badly formed HTTP PROTOCOL in the request, 0.9, 1.0, and 1.1 only - *** Safe, Use [403]
RewriteCond %{THE_REQUEST} !^[A-Z]{3,9}\ .+ HTTP/(0\.9|1\.0|1\.1) [NC]
RewriteRule .* - [F,NS,L]
SPECIFY CHARACTERS
Denies any request for a url containing characters other than "a-zA-Z0-9.+/-?=&" - REALLY helps but may break your site depending on your links. [403]
RewriteCond %{REQUEST_URI} !^/(wp-login\.php|wp-admin/|wp-content/plugins/|wp-includes/).* [NC]
RewriteCond %{THE_REQUEST} !^[A-Z]{3,9}\ [a-zA-Z0-9\.+_/-?=&]+ HTTP/ [NC]
RewriteRule .* - [F,NS,L]
BAD Content Length
Denies any POST request that doesnt have a Content-Length Header - *** Safe, Use [403]
RewriteCond %{REQUEST_METHOD} =POST
RewriteCond %{HTTP:Content-Length} ^$
RewriteCond %{REQUEST_URI} !^/(wp-admin/|wp-content/plugins/|wp-includes/).* [NC]
RewriteRule .* - [F,NS,L]
BAD Content Type
Denies any POST request with a content type other than application/x-www-form-urlencoded|multipart/form-data - *** Safe, Use [403]
RewriteCond %{REQUEST_METHOD} =POST
RewriteCond %{HTTP:Content-Type} !^(application/x-www-form-urlencoded|multipart/form-data.*(boundary.*)?)$ [NC]
RewriteCond %{REQUEST_URI} !^/(wp-login\.php|wp-admin/|wp-content/plugins/|wp-includes/).* [NC]
RewriteRule .* - [F,NS,L]
Directory Traversal
Denies Requests containing ../ or ./. which is a directory traversal exploit attempt - *** Safe, Use [403]
PHPSESSID Cookie
Only blocks when a PHPSESSID cookie is sent by the user and it contains characters other than 0-9a-z - *** Safe, Use [403]
NO HOST:
Denies requests that dont contain a HTTP HOST Header. - *** Safe, Use [403]
RewriteCond %{REQUEST_URI} !^/(wp-login\.php|wp-admin/|wp-content/plugins/|wp-includes/).* [NC]
RewriteCond %{HTTP_HOST} ^$
RewriteRule .* - [F,NS,L]
Bogus Graphics Exploit
Denies obvious exploit using bogus graphics - *** Safe, Use [403]
RewriteCond %{HTTP:Content-Disposition} \.php [NC]
RewriteCond %{HTTP:Content-Type} image/.+ [NC]
RewriteRule .* - [F,NS,L]
No UserAgent, No Post
Denies POST requests by blank user-agents. May prevent a small number of visitors from POSTING. [403]
RewriteCond %{REQUEST_METHOD} =POST
RewriteCond %{HTTP_USER_AGENT} ^-?$
RewriteCond %{REQUEST_URI} !^/(wp-login\.php|wp-admin/|wp-content/plugins/|wp-includes/).* [NC]
RewriteRule .* - [F,NS,L]
No Referer, No Comment
Denies any comment attempt with a blank HTTP_REFERER field, highly indicative of spam. May prevent some visitors from POSTING. [403]
RewriteCond %{THE_REQUEST} ^[A-Z]{3,9}\ /.*/wp-comments-post\.php.* HTTP/ [NC]
RewriteCond %{HTTP_REFERER} ^-?$
RewriteRule .* - [F,NS,L]
Trackback Spam
Denies obvious trackback spam. See Holy Shmoly! [403]
RewriteCond %{REQUEST_METHOD} =POST
RewriteCond %{HTTP_USER_AGENT} ^.*(opera|mozilla|firefox|msie|safari).*$ [NC]
RewriteCond %{THE_REQUEST} ^[A-Z]{3,9}\ /.+/trackback/? HTTP/ [NC]
RewriteRule .* - [F,NS,L]
SSL-Only Site
Redirects all non-SSL (https) requests to your https-enabled url [301]
Anti-Spam, Anti-Exploits
Denies Obvious Spam and uses advanced mod_security protection [Read More]
.htaccess Security Module Screenshot
« .htaccess trick to show Alternate CSS file based on IPApache HTTPD and Module API Versions »

Comments