Redirecting RSS to Feedburner
Apache Environment Variables CGI Script
Surf the net anonymously with Tor
Lets win the DreamHost Contest
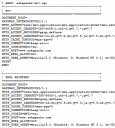
WordPress Plugin for Apache .htaccess Security
- gzip's previous .htaccess file and sends it as an attachment to the logged in users email account along with password user setup.
- Now also works for sites running on SSL (PHP version >4.3.0)
- Rewrote the security module code in the form of snort, nessus, and mod_security rules and signatures
- Added a *real* check to see if mod_rewrite is installed
- Added Modules that remove directoryindexes
- Much more on the way..
Boost SEO, Drive Traffic with the 404 Error Page Plugin
PHP5 Custom Install Shell Script Example
Today I successfully learned how to compile and run multiple custom php installations for a DreamHost account, and to get it working I came upon a simple shell script that I made a couple changes to.
Robots.txt Secrets From Matt Cutts
WordPress What Is This Plugin
CSS Cross-Browser Compatibility Tip
 What I used to do when I was still learning CSS was to check the web page in each of the various problematic browsers to make sure the display stayed the same. I have several actual machines and several vmware virtual machines running various browers but I decided to skip all that extra time and effort and just use an online tool to do it for me. The tool views my page in all the various browsers and generates a screenshot image from each browser so that I can see if there are issues with my CSS.
What I used to do when I was still learning CSS was to check the web page in each of the various problematic browsers to make sure the display stayed the same. I have several actual machines and several vmware virtual machines running various browers but I decided to skip all that extra time and effort and just use an online tool to do it for me. The tool views my page in all the various browsers and generates a screenshot image from each browser so that I can see if there are issues with my CSS.
Prevent WP-Cache from Caching index
Disable caching on WordPress index pages when using WP-Cache with this neat mod to the famously speedy cache plugin.
Best Free Online Banking for Web Professionals
301 Redirect Cheatsheet
 Ultimate Redirect Cheatsheet for multiple programming languages. Redirecting Users with Javascript redirect, meta refresh redirect, and php redirect, also htaccess methods, python, coldfusion, asp, perl, etc.
Ultimate Redirect Cheatsheet for multiple programming languages. Redirecting Users with Javascript redirect, meta refresh redirect, and php redirect, also htaccess methods, python, coldfusion, asp, perl, etc.
Simple PHP Anti-Spam Captcha Script
 Prevent automated web robot tools and spammers from taking advantage of your site with this simple php script that I hacked up earlier today to use on my Advanced HTTP Header Viewer.
Prevent automated web robot tools and spammers from taking advantage of your site with this simple php script that I hacked up earlier today to use on my Advanced HTTP Header Viewer.
Best CSS .Classes for CSS Toolbox
Review: Posh CSS
PoshCSS.com has links to nice and new CSS Articles. Don't worry, they aren't snobs. ;)
Referer Spoofing Using JavaScript
 Even though at the moment I'm more into AJAX and simple behavioural unobtrusive javascript more than java, I still remember how excited I was back in 1995 when Sun released both beta and alpha Java versions to the public.. In fact I still have my Java 1.0 Unleashed book, which I'm looking at right now.
Even though at the moment I'm more into AJAX and simple behavioural unobtrusive javascript more than java, I still remember how excited I was back in 1995 when Sun released both beta and alpha Java versions to the public.. In fact I still have my Java 1.0 Unleashed book, which I'm looking at right now.
Tips on Writing WordPress Plugins
A better way to use PDF files online
The Latest and Greatest php.ini
Grab the latest php.ini developmental version and discover new or previously hidden php runtime configuration settings... ahead of everyone else!
Apache Directives and Modules on DreamHost
Apache .htaccess Directives and Loaded Modules allowed on DreamHost Apache Server 2 Setups.
Renaming Sponsored Links in AdSense
Top Javascript Code Snippets for 2007
Awk Tutorial and Introduction
While researching a unix/linux tool awk I came upon one of the most thorough and helpful tutorials I've ever seen devoted to a particular topic. It's old-school just the way I like it. I contacted the author, Bruce Barnett because I just HAD to have this article for my readers, who are predominantly running solaris/unix/bsd/linux and he kindly gave permission.
What I think about DreamHost Web Hosting
NOTE: This is a very old post, I do NOT recommend DreamHost for anyone other than spammers. They are not a long-term solution.
Using ModSecurity on DreamHost with .htaccess
100 Alternative Search Engines
Updated: AskApache Search Engine Verify
 I just updated the AskApache Search Engine Verify Plugin for WordPress. Short and Sweet, it won't slow down your blog at all, except for the additional crawling of your site by Slurp and Googlebot.
I just updated the AskApache Search Engine Verify Plugin for WordPress. Short and Sweet, it won't slow down your blog at all, except for the additional crawling of your site by Slurp and Googlebot.
The Song from the Ask.com commercial
Pen-testing Security Tools
While testing the exploitability of your target and mapping out vulnerabilities it is important to gain access inside the targets defenses so that you can establish an internal foothold like a owned box or switch. This is so you can use a tool to discover the packet-filtering being used, and literally map out the firewall/IDS rules. Needless to say that really provides you with a lot more complete vulnerability assessment to help discover more weak spots in the system.
The Diary of An American Witchdoctor
Just wanted some bandwidth-free music for the home page~
Updated: WordPress RewriteRules Viewer Plugin
SEO with Robots.txt
Abbr and Acronym examples
Acronym and Abbr examples from the W3C Quality Assurance Site.
Compete Search Analytics officially opened to the public! It rocks!
 I just received an email (I'm a VIP) from the Compete Search Analytics Team announcing that they are officially open to the public! Normally this would have 0 effect on me, I'm not into SEO tools, but this online resource is incredible!
I just received an email (I'm a VIP) from the Compete Search Analytics Team announcing that they are officially open to the public! Normally this would have 0 effect on me, I'm not into SEO tools, but this online resource is incredible!
Random Bits, the podcast that gives you an insiders view
I was over at Alex King's blog today checking out his mobile web plugin for wordpress and I noticed some fresh podcasts from some of the industry's finest. The feeds are .mp3 and are easy to find and browse on the search-this.com site. They have some pretty nice articles over there as well..
Website SEO Score Tool
 Check out this free online SEO site-scoring tool. The SEO generated report is simple, neat, and helpful. The main thing I like about it is how it is a stand-alone website, a residual money making machine.
Check out this free online SEO site-scoring tool. The SEO generated report is simple, neat, and helpful. The main thing I like about it is how it is a stand-alone website, a residual money making machine.
CSS Background Image Sprites
Getting flash to show up in front of content
 I used to have a problem of controlling flash elements on my sites.. On one site we have 6 different flash flv movies that are all the same size and are in the same position on the page. But only 1 is displayed at a time based on what the user wants to watch. So the selected flash movie needs to have the highest stacking order/zIndex.
I used to have a problem of controlling flash elements on my sites.. On one site we have 6 different flash flv movies that are all the same size and are in the same position on the page. But only 1 is displayed at a time based on what the user wants to watch. So the selected flash movie needs to have the highest stacking order/zIndex.






 I've spent a lot of time over the past 10 years managing my money online, and I want to let you all know my two favorite free online banks,
I've spent a lot of time over the past 10 years managing my money online, and I want to let you all know my two favorite free online banks,