Custom Boot Menu in Windows XP
 One of the first things that I do upon receiving a new Windows computer is immediately create a poweruser-style customized boot menu. Then every time I boot I can choose Safe Mode, Recovery Console, Debug, whatever I want! It's quick and easy to set-up and everyone should have one, soo sweet!
One of the first things that I do upon receiving a new Windows computer is immediately create a poweruser-style customized boot menu. Then every time I boot I can choose Safe Mode, Recovery Console, Debug, whatever I want! It's quick and easy to set-up and everyone should have one, soo sweet!
Internet Census 2012 – Port scanning using insecure embedded devices – Carna Botnet
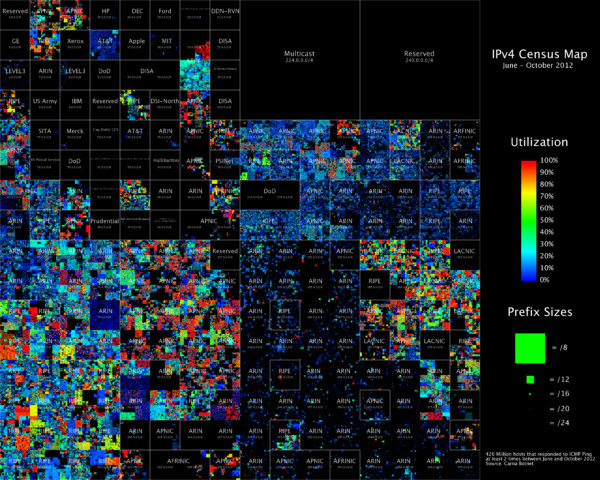 While playing around with the Nmap Scripting Engine (NSE) we discovered an amazing number of open embedded devices on the Internet. Many of them are based on Linux and allow login to standard BusyBox with empty or default credentials. We used these devices to build a distributed port scanner to scan all IPv4 addresses. These scans include service probes for the most common ports, ICMP ping, reverse DNS and SYN scans. We analyzed some of the data to get an estimation of the IP address usage.
While playing around with the Nmap Scripting Engine (NSE) we discovered an amazing number of open embedded devices on the Internet. Many of them are based on Linux and allow login to standard BusyBox with empty or default credentials. We used these devices to build a distributed port scanner to scan all IPv4 addresses. These scans include service probes for the most common ports, ICMP ping, reverse DNS and SYN scans. We analyzed some of the data to get an estimation of the IP address usage.
PortaPutty Auto-Reconnecting SSH Tunnels on an Encrypted TrueCrypt Portable USB Key w GPG
Ok I just came back up to write the intro.. I'm trying to keep it short to avoid getting bogged down by the coolness of each step. Here is what goes on. When I logon to my XP machine at work, I bring my usb key and plug it in first. On logging a window pops up first and it's a password prompt to mount my encrypted drive leonardo. It also checks a keyfile that is located on my usb key, but all I do now is type in my password. That causes my encrypted folder to be accessible to me like a normal drive, and it autoruns a startup batch file.
The batch file causes Portable versions of Firefox (all my bookmarks, my settings) to load, and launches Portable Mozilla Thunderbird (IMAP makes this work well), which is my favorite program (great GPG features and open-source!). Also Some Adobe CS4 software is loaded from the hard drive, like DreamWeaver. In the background, a service we created executes a PortaPuttY plink command to create forwarded tunnels from various remote servers and accounts, all using key-based encryption. These tunnels are automatically reconnected if they are disconnected, meaning you can use a socks 5 if you want or even better!
Hacking VLAN switched networks
 There isn't much vlan info on the net in terms of specifics and I had to learn all about it because I needed to log in to a switch that was on a different vlan. With the help of the Ettercap developers NaGA and ALoR I figured it out.
There isn't much vlan info on the net in terms of specifics and I had to learn all about it because I needed to log in to a switch that was on a different vlan. With the help of the Ettercap developers NaGA and ALoR I figured it out.
Originally Posted: 3/30/2004
COMPUTER SECURITY TOOLBOX
List of mainly obscure security software geared more for the master pentester. These are mostly for unix, bsd, and mac and many are difficult to install and setup (require custom servers, inside access points, obscure libraries). Only programs that output data are included, so no actual exploits or anything. Most of these output extremely useful albeit extremely technical information.Crazy POWERFUL Bash Prompt
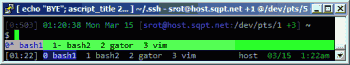 This amazing bash linux prompt does more than meets the eye. If you want to know how to become really good with technology, linux is the secret sauce behind the AskApache articles. Open Source is elixir of the web. Thanks to everyone who helped me for the past 20 years. I use linux/bsd because homey don't play, so this is geared to be as productive a prompt as I can make it.
This amazing bash linux prompt does more than meets the eye. If you want to know how to become really good with technology, linux is the secret sauce behind the AskApache articles. Open Source is elixir of the web. Thanks to everyone who helped me for the past 20 years. I use linux/bsd because homey don't play, so this is geared to be as productive a prompt as I can make it.
Don't have much time.. or just don't care? Not a problem, here are the 3 lines to copy and paste - you can just paste them right in your shell to test it, or add to a startup script.
export AA_P="export PVE=\"\\033[m\\033[38;5;2m\"\$(( \`sed -n \"s/MemFree:[\\t ]\\+\\([0-9]\\+\\) kB/\\1/p\" /proc/meminfo\` / 1024 ))\"\\033[38;5;22m/\"\$((\`sed -n \"s/MemTotal:[\\t ]\\+\\([0-9]\\+\\) kB/\\1/p\" /proc/meminfo\`/ 1024 ))MB\"\\t\\033[m\\033[38;5;55m\$(< /proc/loadavg)\\033[m\";echo -en \"\""
export PROMPT_COMMAND="history -a;((\$SECONDS % 10==0 ))&&eval \"\$AA_P\";echo -en \"\$PVE\";"
export PS1="\\[\\e[m\\n\\e[1;30m\\][\$\$:\$PPID \\j:\\!\\[\\e[1;30m\\]]\\[\\e[0;36m\\] \\T \\d \\[\\e[1;30m\\][\\[\\e[1;34m\\]\\u@\\H\\[\\e[1;30m\\]:\\[\\e[0;37m\\]\${SSH_TTY} \\[\\e[0;32m\\]+\${SHLVL}\\[\\e[1;30m\\]] \\[\\e[1;37m\\]\\w\\[\\e[0;37m\\] \\n(\$SHLVL:\\!)\\\$ " && eval $AA_P
ListOfErrors
Libcurl Error Codes

Fsockopen Magic
 PHP's fsockopen function lets you open an Internet or Unix domain socket connection for connecting to a resource, and is one of the most powerful functions available in the php language.
PHP's fsockopen function lets you open an Internet or Unix domain socket connection for connecting to a resource, and is one of the most powerful functions available in the php language.
Port Redirector
can you please suggest me any tiny and good port redirector for linux and unix like oses ? so that when I connect to the box to a given port it redirects my connection to another box and port that I can chose ? thanx a lotFastCGI on DreamHost
Using FastCGI on DreamHost and .htaccess
Top 5 Vulnerability Port Scanners
Asked some hackers and Computer Security gurus to list their 5 favorite Vulnerability/Port Scanners. Here are the results.Actual Htaccess Files from My Server
#### No https except to wp-admin -
# If the request is empty ( implies fopen or normal file access by a php script )
RewriteCond %{THE_REQUEST} ^$ [OR]
# OR if the request if for wp-admin or wp-login.php
RewriteCond %{REQUEST_URI} ^/(wp-admin|wp-login.php).*$ [NC,OR]
# OR if the Referer is https
RewriteCond %{HTTP_REFERER} ^https://www.askapache.com/.*$ [NC]
# THEN skip the following rule, basically all this does is force https or badhost to be redirected
# BUT because of the above 3 rewritecond's, this won't break poorly written admin scripts
RewriteRule .* - [S=1]
RewriteCond %{HTTPS} =on [OR]
RewriteCond %{HTTP_HOST} !^www.askapache.com$ [NC]
RewriteRule .* https://www.askapache.com%{REQUEST_URI} [R=301,L]
RewriteCond %{THE_REQUEST} ^[A-Z]{3,9} /(wp-admin/.*|wp-login.php.*) HTTP/ [NC]
RewriteCond %{HTTPS} !=on
RewriteRule .* https://%{SERVER_NAME}%{REQUEST_URI} [R=301,L]
Apache SSL in htaccess examples
SSLOptions +StrictRequire
SSLRequireSSL
SSLRequire %{HTTP_HOST} eq "google.com"
ErrorDocument 403 https://google.com
Some of the Ins and Outs of using SSL Connections with Apache.
Advanced Windows Batch File Scripting
![]() If for some reason you need to use windows .bat batch file scripting to do some task, or you just want to learn the most universal batch programming language on Windows machines, you lucked out and found the AskApache example. My expertise is the shell, in this article the shell is Windows
If for some reason you need to use windows .bat batch file scripting to do some task, or you just want to learn the most universal batch programming language on Windows machines, you lucked out and found the AskApache example. My expertise is the shell, in this article the shell is Windows cmd.exe. It has some pretty advanced windows shell usage, including pipes and redirection, but it's the modular linux-like coding approach that earns this script it's "advanced" title.
:SETPROMPT set PROMPT=$_[%USERNAME%@%USERDOMAIN%]$S[$P]$_$M$G && EXIT /B
![]() My favorite tool (and I've tried sooo many) for editing most Windows files and especially .bat files is the free and open-source Notepad++. Set that up and you will have a color-syntax-highlighted editor for Batch Scripting that works very very well.
My favorite tool (and I've tried sooo many) for editing most Windows files and especially .bat files is the free and open-source Notepad++. Set that up and you will have a color-syntax-highlighted editor for Batch Scripting that works very very well.
Undetectable Sniffing On Ethernet
 I have been in some tight spots where I had to sniff a password or two off the wire, or sniff some packets off the wire and based on the packets content perform some action... Accidentally, I stumbled on a method to sniff data while remaining undetected and invisible.
I have been in some tight spots where I had to sniff a password or two off the wire, or sniff some packets off the wire and based on the packets content perform some action... Accidentally, I stumbled on a method to sniff data while remaining undetected and invisible.
Originally Posted: 2003/04/15
Advanced WordPress wp-config.php Tweaks
The bottom line for this article is that I want to make WordPress as fast, secure, and easy to install, run, and manage because I am using it more and more for client production sites, I will work for days in order to solve an issue so that I never have to spend time on that issue again. Time is money in this industry and that is ultimately (time) what there is to gain by tweaking WordPress.
Note: I spent no time on readability, this is primarily a read the code and figure it out article.. This is for advanced users looking for a reference or discussion and for those of you looking to advance. Feedback would be great if you make it that far..
Htaccess Mod_Rewrite – Crazy Advanced Master Class
 htaccess rewrite Master Class! If you understand the basics of mod_rewrite, or if you literally write the mod_rewite.c code, this article will transform your thinking. The transformation is profound. Deeply effective. Culmination of the best of the best mod_rewrite tricks for understanding and learning exactly what rewrite is doing.
htaccess rewrite Master Class! If you understand the basics of mod_rewrite, or if you literally write the mod_rewite.c code, this article will transform your thinking. The transformation is profound. Deeply effective. Culmination of the best of the best mod_rewrite tricks for understanding and learning exactly what rewrite is doing.
IP Abuse Detection for DreamHost
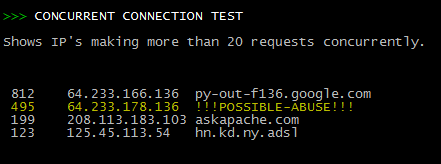 Scan Apache logs for IP address that are probably evil, then generates an .htaccess file to DENY them all.
Scan Apache logs for IP address that are probably evil, then generates an .htaccess file to DENY them all.
If you can crash your daemon, you likely have a security problem
Tons of awesome tips and tricks using netcat. Port redirector, nessus wrapper, capture exploits being sent by vuln scanners, etc. This is very useful for doing stuff like redirecting traffic through your firewall out to other places like web servers and mail hubs, while posing no risk to the firewall machine itself.
Speed Up Sites with htaccess Caching
2 awesome ways to implement caching on your website using Apache .htaccess or httpd.conf. Both methods are extremely simple to set up and will dramatically speed up your site!THE Ultimate Htaccess
 .htaccess is a very ancient configuration file for web servers, and is one of the most powerful configuration files most webmasters will ever come across. This htaccess guide shows off the very best of the best htaccess tricks and code snippets from hackers and server administrators.
.htaccess is a very ancient configuration file for web servers, and is one of the most powerful configuration files most webmasters will ever come across. This htaccess guide shows off the very best of the best htaccess tricks and code snippets from hackers and server administrators.
You've come to the right place if you are looking to acquire mad skills for using .htaccess files!
Notes from Apache HTTPD Source Code
thought I'd take a break from coding and post about how open-source is such a great tool for finding the best answers to the toughest questions,
/** is the status code informational */ #define ap_is_HTTP_INFO(x) (((x) >= 100)&&((x) < 200)) /** is the status code OK ?*/ #define ap_is_HTTP_SUCCESS(x) (((x) >= 200)&&((x) < 300)) /** is the status code a redirect */ #define ap_is_HTTP_REDIRECT(x) (((x) >= 300)&&((x) < 400)) /** is the status code a error (client or server) */ #define ap_is_HTTP_ERROR(x) (((x) >= 400)&&((x) < 600)) /** is the status code a client error */ #define ap_is_HTTP_CLIENT_ERROR(x) (((x) >= 400)&&((x) < 500)) /** is the status code a server error */ #define ap_is_HTTP_SERVER_ERROR(x) (((x) >= 500)&&((x) < 600)) /** is the status code a (potentially) valid response code? */ #define ap_is_HTTP_VALID_RESPONSE(x) (((x) >= 100)&&((x) < 600))
PDF.js
 pdf.js is an HTML5 technology experiment that explores building a faithful and efficient Portable Document Format (PDF) renderer without native code assistance.
pdf.js is an HTML5 technology experiment that explores building a faithful and efficient Portable Document Format (PDF) renderer without native code assistance.
Upgrading to DreamHost Private Servers
DreamHost PS gives you your own "virtual machine", protecting your CPU and RAM on your physical machine for faster websites. Here's what I like and dislike about DreamHostPS, and some of the issues and solutions for migrating.
IP Blocked by stateful Firewall, now what?
On-Demand MySQL Backup Shell Script
On-Demand WordPress MySQL database Backup Shell Script for DreamHostApache Directives and Modules on DreamHost
Apache .htaccess Directives and Loaded Modules allowed on DreamHost Apache Server 2 Setups.
King Penguin Linux Notebook
 The machine itself is super super ultra-thin, wafer thin, very cool looking. It's crazy light, I was amazed how slick it looked when it arrived.
The machine itself is super super ultra-thin, wafer thin, very cool looking. It's crazy light, I was amazed how slick it looked when it arrived.
Huge amount of open-source hardware/chipsets/etc.. The first time I went through the dmesg I was smiling. 2 USB 3.0 ports, and they actually work as promised, very very fast transfer speeds to my USB 3.0 external SSD. Incredible speed, boot time is the fastest I've ever seen. Starts at $720, mine was $1,800
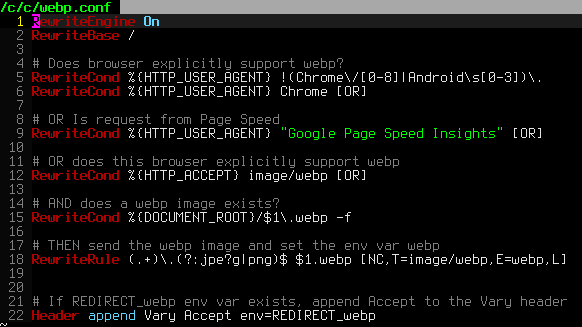
Serving WebP images for PNG and JPG files
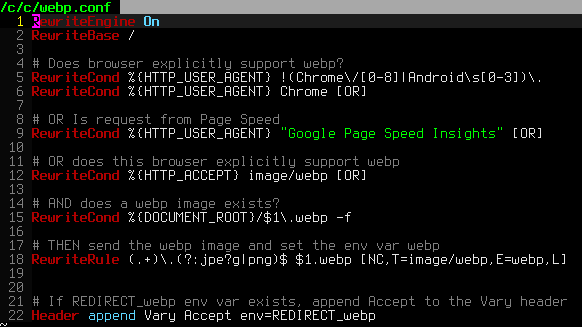 One of the biggest speed bottlenecks of sites today are images, specifically unoptimized images or large scaled images. With Apaches Rewrite module we can convert all existing jpegs and png files (and most gifs) to webp, then transparently rewrite them so that a request for img.png from a browser that supports webp will receive img.webp.
One of the biggest speed bottlenecks of sites today are images, specifically unoptimized images or large scaled images. With Apaches Rewrite module we can convert all existing jpegs and png files (and most gifs) to webp, then transparently rewrite them so that a request for img.png from a browser that supports webp will receive img.webp.
3 Ways to Serve PDF Files using Htaccess Cookies, Headers, Rewrites
FYI, using the Mod_Rewrite Variables Cheatsheet makes this example, and all advanced .htaccess code easier to understand. This demo lets you set a cookie with 1 of 3 values, then you just request the pdf file with a normal link click and get 1 of 3 different responses. This is accomplished with a nice bit of .htaccess code.
Set PDF Viewing Mode - Make a selection, then click the view pdf button.
Inline Download Save As View PDF using selected mode »
Mod_Status tricks to View Apache Module Directives
 Quick and easy method to get a list of all Apache Modules currently loaded, a list of all the directives each module provides, a list of currently used directives, etc... These directives can be used in httpd.conf and/or .htaccess files so it is definately useful to know which ones are available and which ones are currently being used.
Quick and easy method to get a list of all Apache Modules currently loaded, a list of all the directives each module provides, a list of currently used directives, etc... These directives can be used in httpd.conf and/or .htaccess files so it is definately useful to know which ones are available and which ones are currently being used.
Shell Scripts for Dreamhost
Example shell scripts (bash or sh) that automate and easyate tasks from within the dreamhost ssh env
Optimizing Servers and Processes for Speed with ionice, nice, ulimit
To prepare for several upcoming articles on AskApache that are focused on optimizing Servers and Sites from a server admin level, here is an article to introduce the main tools that we will be using. These tools are used to optimize CPU time for each process using nice and renice, and other tools like ionice are used to optimize the Disk IO, or Disk speed / Disk traffic for each process. Then you can make sure your mysqld and httpd processes are always fast and prioritized.
Terminal Escape Code Zen
An image and technicacl achievement so profound, it will touch yoour heart.. So 3D... it'll hurt you eyes! LOL.. lol.. Man I am cracking up here. haha Ha definately the best intro ever, those really do look 3D for terminal though huh.. Sweet. Here is the little function I wrote to output that grey marble.
Mod_Rewrite Variables Cheatsheet
 We've figured out what mod_rewrite variables look like, a cheatsheet of the actual value.
We've figured out what mod_rewrite variables look like, a cheatsheet of the actual value.
SPF Records on DreamHost
Here are the steps that I take to get an SPF Record going on DreamHost
v=spf1 mx ip4:64.111.100.0/24 ip4:66.33.201.0/24 ip4:66.33.216.0/24 ip4:208.97.1 32.0/24 ip4:208.97.187.0/24 ip4:208.113.200.0/24 ip4:208.113.244.0/24 ip4:64.18.0.0/20 ip4:74.125.148.0/22 include:aspmx.googlemail.com include:_spf.google.com ~all
Questions I Ask Web Hosting Companies, Before Buying
The following is a transcript of a chat I had with a company called tektonic, and at that time I was looking for a cheap linux host to use for some redundancy/failover operations. I generally contact a new hosting company like this every few months.. I like to have options available in case of some kind of failure or network attack, so it's always a good idea to have a few ace linux servers in your back pocket.
If you've read any other articles on AskApache, you can see a certain obsession towards optimization, speed, and security -- so that is the purpose of the following questions.